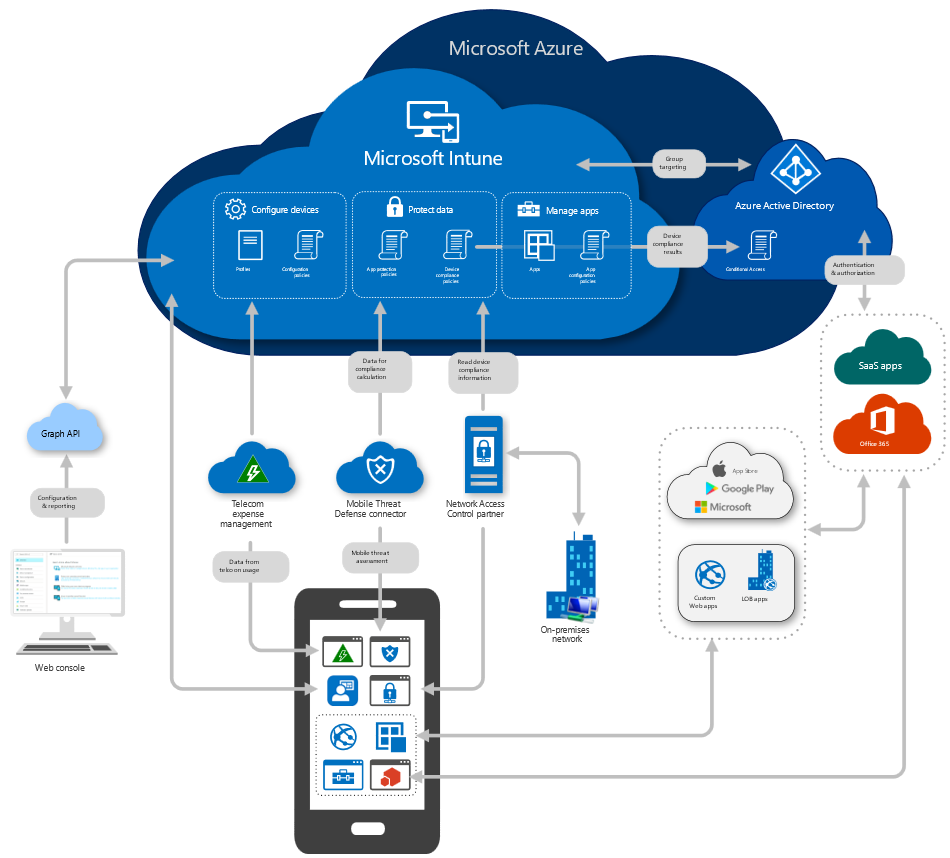
How to Use Microsoft Intune to Secure and Manage Mobile Devices
In the modern business landscape, managing mobile devices has become a critical aspect of maintaining security and productivity. Microsoft Intune emerges as a comprehensive solution, enabling organizations to efficiently manage and secure their mobile devices. In this step-by-step guide, we’ll walk you through the process of using Microsoft Intune to manage your mobile devices effectively.
What is Microsoft Intune?
Microsoft Intune is a cloud-based mobile device management (MDM) and mobile application management (MAM) service that helps organizations control access to corporate resources and secure data on mobile devices.
Step 1: Set Up Microsoft Intune:
- Access the Intune Dashboard: Log in to the Microsoft 365 Admin Center and navigate to the Intune dashboard.
- Set Up Device Enrollment: Configure device enrollment settings, including platforms like iOS, Android, and Windows.
Step 2: Enroll Devices:
- User Enrollment: Users can enroll their devices by accessing the Intune Company Portal app on their devices.
- Bulk Enrollment: For corporate-owned devices, use methods like Apple’s Device Enrollment Program (DEP) or Android Enterprise to enroll devices in bulk.
http://informationarray.com/2023/08/16/maximizing-big-data-insights-with-apache-parquet-efficient-data-storage-and-analytics/
Step 3: Apply Device Policies:
- Create Device Profiles: Define policies for different types of devices, specifying security settings, app installations, and network configurations.
- Assign Profiles: Assign device profiles to user groups or individual users to ensure proper policy application.
Step 4: Manage Apps:
- App Deployment: Use Intune to deploy required apps to devices, ensuring users have the necessary tools to carry out their tasks.
- App Protection Policies: Implement policies that protect corporate data within apps, preventing data leakage.
Step 5: Monitor and Secure Devices:
- Monitor Device Compliance: Intune provides insights into device compliance status, allowing you to identify non-compliant devices.
- Remote Actions: Take actions remotely, such as locking a device, wiping data, or resetting passcodes.
Step 6: Monitor and Analyze:
- Reports and Insights: Utilize Intune’s reporting capabilities to monitor device usage, compliance, and security.
- Continuous Improvement: Use the insights gained from reports to refine policies and enhance device management strategies.
Microsoft Intune offers a comprehensive platform for managing mobile devices, streamlining security, and enhancing productivity. By following this step-by-step guide, you can harness the power of Intune to efficiently enroll, manage, secure, and monitor your mobile devices. With Intune’s capabilities at your fingertips, you can navigate the complexities of mobile device management with confidence, ensuring a seamless and secure mobile experience for your organization.